支付宝AR红包研究
最近支付宝AR红包很火的样子,安全客上就更新了好几次破解方法。尝试从线索中的图片恢复图片,然后用摄像头扫描,发现成功率越来越低,一是因为线索图片中的条纹比刚出来的时候多,二是因为线索图片的像素由原来的200*200变成了100*100。
试了好几次都不成功的情况下,我开始怀疑用摄像头扫描可能受像素、亮度、角度等因素影响,发送给支付宝服务器的图片和原图相差太大。于是我尝试用hook的方式,直接上传恢复后的图片,看能否成功…
用cydia hook fopen函数,打印出文件名,日志内容大概如下:
| 12-27 21:59:46.063 12475-18005/? D/NATIVEHOOK﹕ !!: /storage/emulated/0/amap/data/cache/vmap4tiles/standard.dat r+b
12-27 21:59:46.083 12475-17171/? D/NATIVEHOOK﹕ !!: /storage/emulated/0/alipay/multimedia/b930exxxxxxxxxxxxxx/c0/2iibx3cvcdimlimq02icnpsoj rb
12-27 22:01:05.723 19549-30435/? D/NATIVEHOOK﹕ !!: /proc/net/xt_qtaguid/iface_stat_fmt r
12-27 22:01:05.723 19549-30435/? D/NATIVEHOOK﹕ !!: /proc/net/xt_qtaguid/iface_stat_fmt r
12-27 22:01:07.493 19549-30459/? D/NATIVEHOOK﹕ !!: /data/data/com.eg.android.AlipayGphone/cache/image_up_1896222xxx.jpg rb
12-27 22:01:07.733 19549-30430/? D/NATIVEHOOK﹕ !!: /proc/19549/stat rb
12-27 22:01:07.733 19549-30430/? D/NATIVEHOOK﹕ !!: /proc/19549/stat rt
|
其中文件/storage/emulated/0/alipay/multimedia/b930exxxxxxxxxxxxxx/c0/2iibx3cvcdimlimq02icnpsoj为线索或头像之类的图片, /data/data/com.eg.android.AlipayGphone/cache/image_up_1896222xxx.jpg为扫描时上传给支付宝服务器的图片。
所以在fopen的hook 函数中,对文件名进行检测,当文件名中包含cache/image_up时,就让fopen去读一个指定好的文件。代码实现如下:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
| int my_fopen( char * filename, char * mode )
{
int uid = 0;
FILE * inputfile;
FILE * outfile;
int timestamp;
int length;
char * buf;
char newfilename[256] = { 0 };
uid = getuid();
if ( uid == 10089 )
{
if ( strstr( filename, "com.eg.android.AlipayGphone/cache/image_up" ) )
{
filename = "/data/local/tmp/new.jpg";
}
if ( strstr( filename, "/alipay/multimedia/" ) && strcmp( "rb", mode ) == 0 )
{
timestamp = (int) time( NULL );
inputfile = (FILE *) old_fopen( filename, mode );
if ( inputfile )
{
LOGD( "!!: Save Images..." );
fseek( inputfile, 0, SEEK_END );
length = ftell( inputfile );
fseek( inputfile, 0, SEEK_SET );
buf = (char *) malloc( length );
fread( buf, length, 1, inputfile );
fclose( inputfile );
sprintf( newfilename, "%s%d.jpg", "/storage/emulated/0/alipay/images/", timestamp );
outfile = (FILE *) old_fopen( newfilename, "wb" );
fwrite( buf, length, 1, outfile );
fclose( outfile );
free( buf );
}
}
LOGD( "!!: %s\t%s", filename, mode );
}
return(old_fopen( filename, mode ) );
}
|
对一些图片进行上传测试,其中最后一张是最接近原图的,第二排的1,2,3,4张是用线索图片恢复出来的…
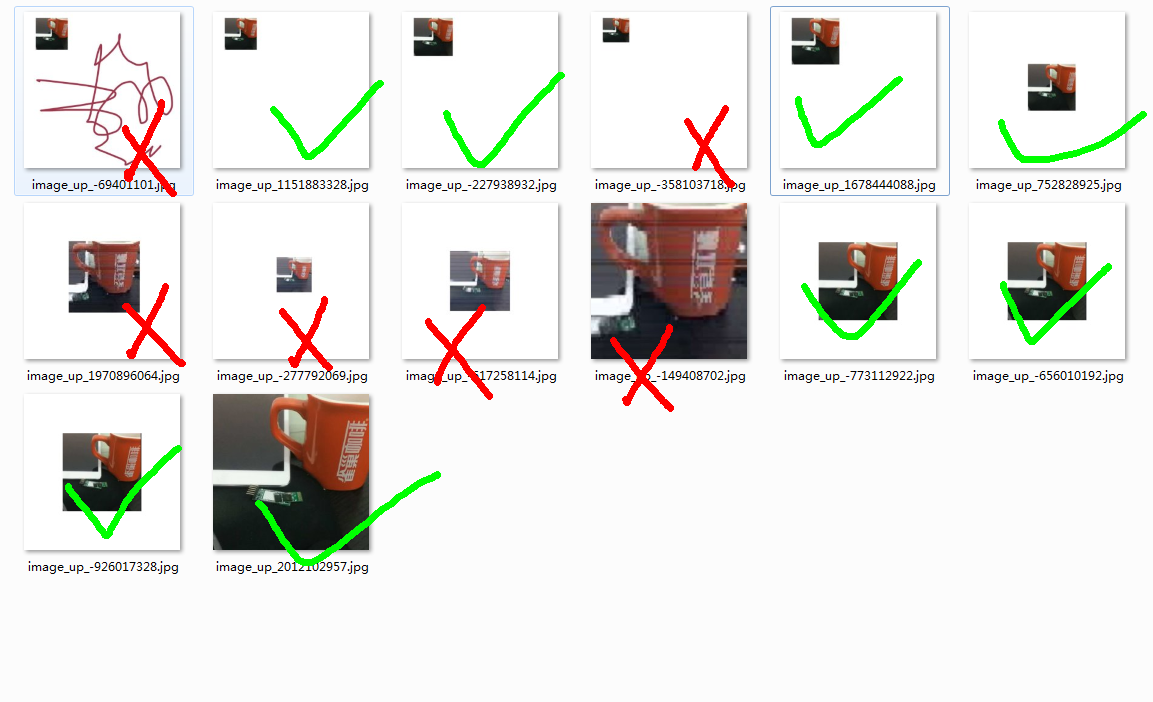
所以,现在网上流传的各种图片还原方法感觉都不是很有效,坐等更高级的图片还原方法…………
