IDA keygen
IDA keygen
IDA uses RSA-1024 for its key signatures and without the private key you
cannot make valid keys. So what I did was to generate a new pair of
public/private keys with a modulus close to the original. The two RSA
modulus differ by just one byte. This was important becauseIDA checks the validity of the modulus and private key but it only compares the first and last bytes.This allows one to patch just one byte in the IDA library and
have complete control of the license. This works for all OS versions: Mac,
Linux and Windows. I’m sure that after this keygen is published (last IDA
version is now 7.3) better checks will be incorporated and the binaries
will have to be patched more extensively.
使用shell脚本随机生成1024位的RSA密钥,检查N的首位和末位,直到生成满足条件的密钥。
1 | |
查看P,Q:
1 | |
计算私钥D:
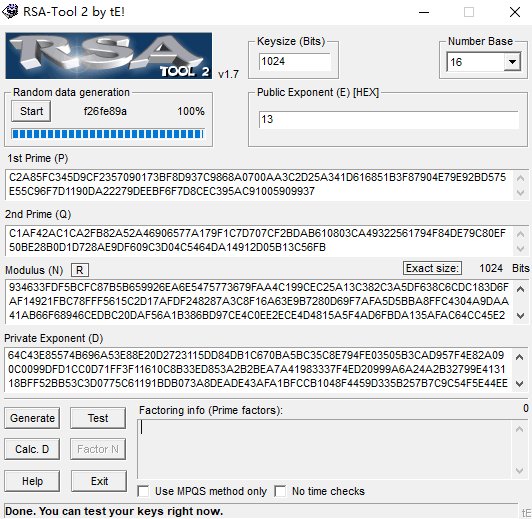
RSA参数:
P: C2A85FC345D9CF2357090173BF8D937C9868A0700AA3C2D25A341D616851B3F87904E79E92BD575E55C96F7D1190DA22279DEEBF6F7D8CEC395AC91005909937
Q: C1AF42AC1CA2FB82A52A46906577A179F1C7D707CF2BDAB610803CA49322561794F84DE79C80EF50BE28B0D1D728AE9DF609C3D04C5464DA14912D05B13C56FB
N: 934633FDF5BCFC87B5B659926EA6E5475773679FAA4C199CEC25A13C382C3A5DF638C6CDC183D6FAF14921FBC78FFF5615C2D17AFDF248287A3C8F16A63E9B7280D69F7AFA5D5BBA8FFC4304A9DAA41AB66F68946CEDBC20DAF56A1B386BD97CE4C0EE2ECE4D4815A5F4AD6FBDA135AFAC64CC45E21DE32B8A117579F822B2ED
E: 13
D: 64C43E85574B696A53E88E20D2723115DD84DB1C670BA5BC35C8E794FE03505B3CAD957F4E82A090C0099DFD1CC0D71FF3F11610C8B33ED853A2B2BEA7A41983337F4ED20999A6A24A2B32799E413118BFF52BB53C3D0775C61191BDB073A8DEADE43AFA1BFCCB1048F4459D335B257B7C9C54F5E44EE888A26A7F95701241DF
N-reverse: EDB222F87975118A2BE31DE245CC64ACAF35A1BD6FADF4A515484DCE2EEEC0E47CD96B381B6AF5DA20BCED6C94686FB61AA4DAA90443FC8FBA5B5DFA7A9FD680729B3EA6168F3C7A2848F2FD7AD1C21556FF8FC7FB2149F1FAD683C1CDC638F65D3A2C383CA125EC9C194CAA9F67735747E5A66E9259B6B587FCBCF5FD334693
签名:
key = lic**D mod N
验证:
lic = key**E mod N
lic为key明文读取后的结构体。
参考链接: