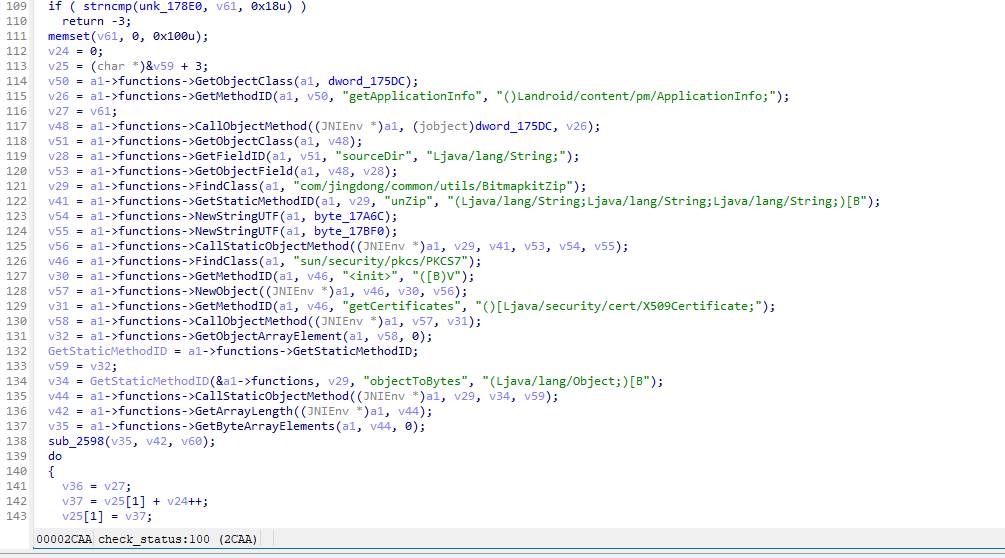
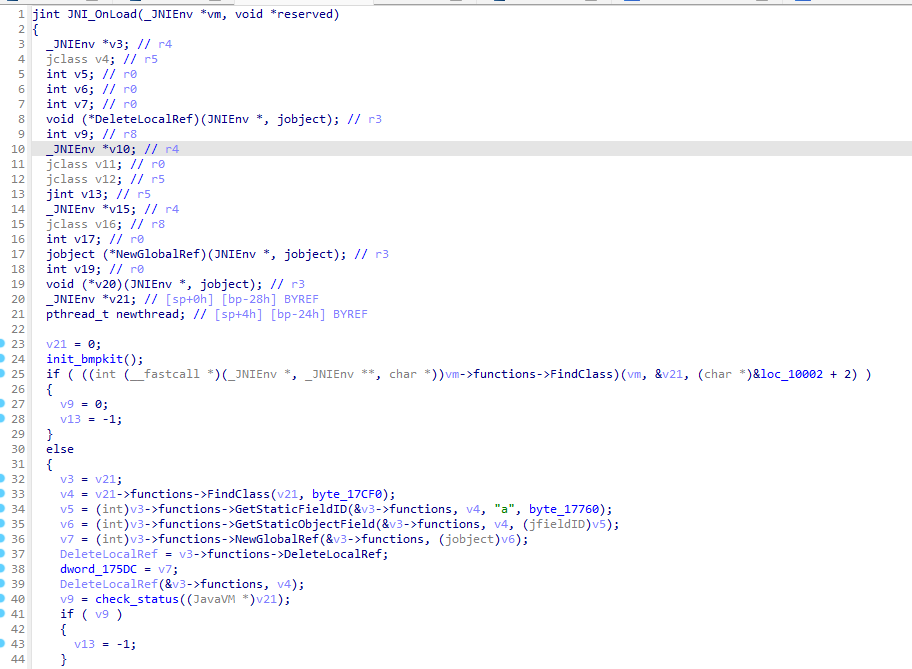
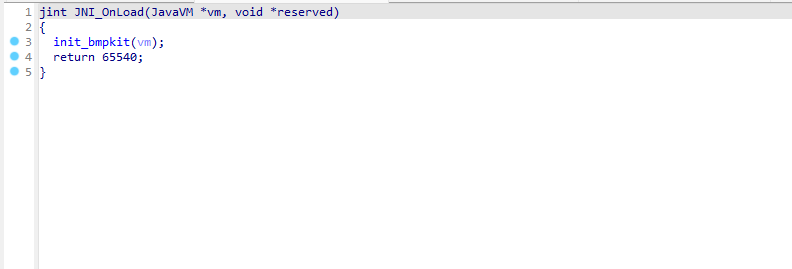
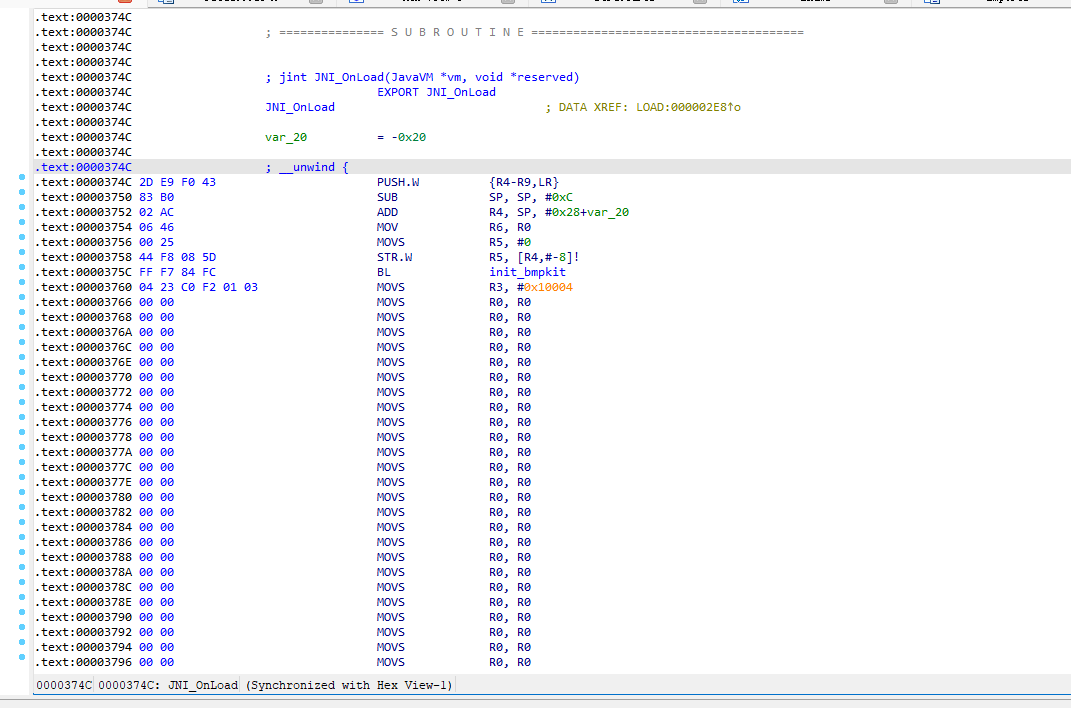
package com.jingdong.mall.app;
import com.github.unidbg.AndroidEmulator;
import com.github.unidbg.Emulator;
import com.github.unidbg.arm.context.RegisterContext;
import com.github.unidbg.hook.hookzz.HookEntryInfo;
import com.github.unidbg.hook.hookzz.HookZz;
import com.github.unidbg.hook.hookzz.IHookZz;
import com.github.unidbg.hook.hookzz.WrapCallback;
import com.github.unidbg.linux.android.AndroidEmulatorBuilder;
import com.github.unidbg.linux.android.AndroidResolver;
import com.github.unidbg.linux.android.dvm.DalvikModule;
import com.github.unidbg.linux.android.dvm.DvmClass;
import com.github.unidbg.linux.android.dvm.StringObject;
import com.github.unidbg.linux.android.dvm.VM;
import com.github.unidbg.linux.android.dvm.jni.ProxyClassFactory;
import com.github.unidbg.linux.android.dvm.jni.ProxyDvmObject;
import com.github.unidbg.memory.Memory;
import com.github.unidbg.utils.Inspector;
import com.sun.jna.Pointer;
import java.io.File;
import java.io.IOException;
import java.nio.charset.StandardCharsets;
import java.util.HashMap;
import java.util.Map;
public class SignUtil {
private final AndroidEmulator emulator;
private final DvmClass BitmapkitUtils;
private final VM vm;
public SignUtil() {
emulator = AndroidEmulatorBuilder.for32Bit()
.setProcessName("com.jingdong.mall.app")
.build();
Memory memory = emulator.getMemory();
memory.setLibraryResolver(new AndroidResolver(23));
vm = emulator.createDalvikVM();
vm.setDvmClassFactory(new ProxyClassFactory());
vm.setVerbose(false);
DalvikModule dm = vm.loadLibrary(new File("unidbg-android/src/test/resources/example_binaries/armeabi-v7a/test.so"), false);
BitmapkitUtils = vm.resolveClass("com/jingdong/common/utils/BitmapkitUtils");
dm.callJNI_OnLoad(emulator);
IHookZz hookZz = HookZz.getInstance(emulator);
System.out.println(String.format("0x%x",dm.getModule().findSymbolByName("Java_com_jingdong_common_utils_BitmapkitUtils_getSignFromJni").getAddress()));
hookZz.wrap(dm.getModule().base+0x10DE5,new WrapCallback<RegisterContext>() {
@Override
public void preCall(Emulator<?> emulator, RegisterContext ctx, HookEntryInfo info) {
Pointer pointer = ctx.getPointerArg(2);
int length = ctx.getIntArg(3);
byte[] key = pointer.getByteArray(0, length);
Inspector.inspect(key, "");
System.out.println(length);
}
});
hookZz.wrap(dm.getModule().base+0x18b9,new WrapCallback<RegisterContext>() {
@Override
public void preCall(Emulator<?> emulator, RegisterContext ctx, HookEntryInfo info) {
Pointer pointer = ctx.getPointerArg(1);
int length = ctx.getIntArg(2);
byte[] key = pointer.getByteArray(0, length);
Inspector.inspect(key, "calc");
System.out.println();
}
});
hookZz.wrap(dm.getModule().base+0x227d,new WrapCallback<RegisterContext>() {
@Override
public void preCall(Emulator<?> emulator, RegisterContext ctx, HookEntryInfo info) {
Pointer pointer = ctx.getPointerArg(0);
int length = ctx.getIntArg(1);
byte[] key = pointer.getByteArray(0, length);
Inspector.inspect(key, "get_md5_input");
System.out.println();
}
});
}
public void destroy() throws IOException {
emulator.close();
}
public String getSignFromJni(Object p1, String p2, String p3, String p4,String p5,String p6) {
String methodSign = "getSignFromJni(Landroid/content/Context;Ljava/lang/String;Ljava/lang/String;Ljava/lang/String;Ljava/lang/String;Ljava/lang/String;)Ljava/lang/String;";
StringObject obj = BitmapkitUtils.callStaticJniMethodObject(emulator, methodSign, p1, p2, p3, p4,p5,p6);
return obj.getValue();
}
public static void main(String[] args) throws Exception {
SignUtil signUtil = new SignUtil();
String sign = signUtil.getSignFromJni(null, "1","2","3","4","5");
System.out.println(sign);
}
}