Cloudflare TLS Fingerprints Bypass 使用Python,curl请求https://dash.cloudflare.com修改网站配置,出现如下错误信息:
{"result" : null ,"success" : false ,"errors" : ["code" : 1041 ,"message" : "We cannot process this request as we suspect it was automated. Contact support for more information." "messages" : []
Cloudflare使用了类似JA3 的TLS指纹检测,并开源(mitmengine )。
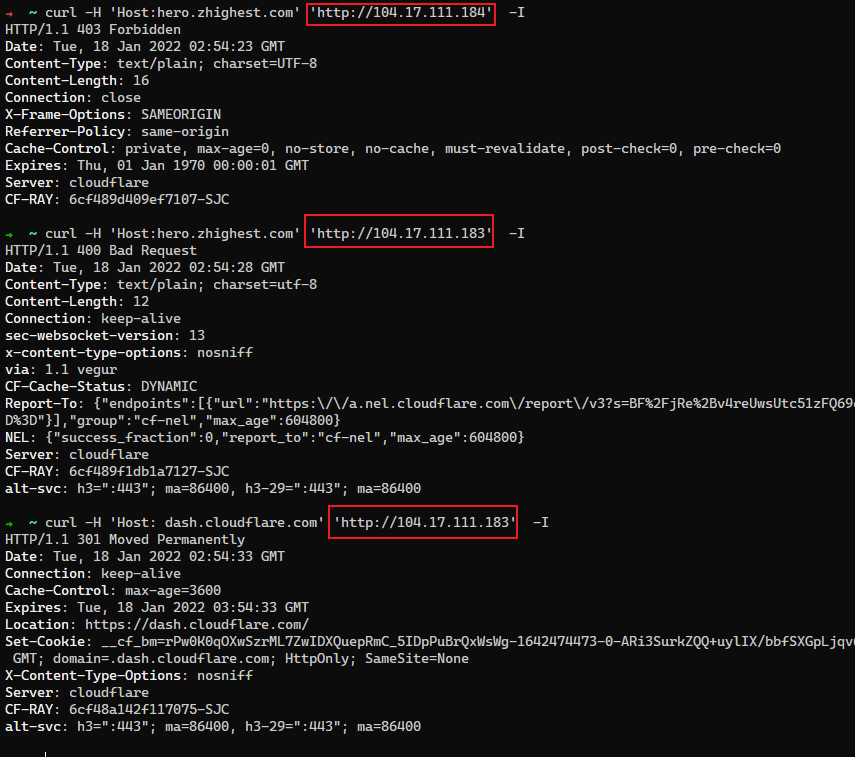
使用17ce.com查看dash.cloudflare.com对应的IP,有两个独立IP:
104.17.110.184
直接访问这个IP会出现错误,且错误和Cloudflare CDN节点IP一致。
➜ ~ curl 104.17.111.184
测试后发现dash.cloudflare.com也使用了CF自己的CDN,只是节点是单独的,猜测是为了自身产品的稳定性。也可以通过通用的节点IP访问dash.cloudflare.com。
无意中发现可通过Cloudflare的workers直接访问dash.cloudflare.com(绕过TLS指纹检测).
addEventListener("fetch" ,event =>let url=new URL(event.request.url);"dash.cloudflare.com" ;let request=new Request(url,event.request);