云闪付逆向笔记
云闪付逆向笔记
流程:
获取券号
couponId初始化验证码(
/youhui-web/restlet/frog/initCaptcha),获取验证码的必要参数,请求参数与响应结果均加密。请求参数为billId, 是couponId加密后的结果。响应结果解密后包含dfpSessionId,sessionId参数。1
2
3
4
5
6encrypt('3102022051863931')
encrypt result: 0F94DD568A40DAE4D669A1F55A786D95
resp = 'a97faad1644995b73ed282dee397aa132c453a978cc46a29653691a62b111a8d86b1d1fee21fe4f85c8527c2b9ba17661fb8589624bf17d027ac0f26195f6742feeaa25bc0be0212e1405e8d1686f20a59153713cb8c91dcf3f1ca221370c164fb89362107127be29c286ef73f8602414c7bd9780b1842f3875c2d4f5c4223241a653ac94b5208ae9686b5172b9cbf08ae4b49313fcb425a833c13f09ae9443688edfc16b7bd035d67345e7ec21403a1ab6b9e23644005595f23cb3c96aa0034'
derypt(resp)
decrypt result: {"msg":"success","resp":"00","cmd":"frog/initCaptcha","params":{"hexStr":"","dfpSessionId":"110005D001L0VAdpjbl1TKOIPPiX11653287554405","id":"","sessionId":"7c7488a80884414b8459da411b2880af"}}获取验证码
capId1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16GET /session/initcap?callback=jsonpCallbackyyyy0523164902432_wHG4P7d7w910Rdj&v=1653295742429&cType=3&cVersion=1.0.0&sesId=4cdd249449f14eb5b4eef41086bd7f61 HTTP/1.1
Host: captcha.95516.com
---------------
HTTP/1.1 200 OK
Date: Mon, 23 May 2022 08:49:02 GMT
Content-Type: application/json;charset=UTF-8
Connection: close
Server: nginx
X-Frame-Options: SAMEORIGIN
X-Via: 1.1 xin151:5 (Cdn Cache Server V2.0)
X-Ws-Request-Id: 628b4a7e_xin151_20427-6065
Content-Length: 218
jsonpCallbackyyyy0523164902432_wHG4P7d7w910Rdj({"resCode":"0000","resMsg":"成功","resData":{"dVersion":"2.0.0","capInfo":"27.0","capType":"4","capId":"e1fed7b26f764a94b37767aeb2bf22a7"},"extensions":{},"dealTime":2})使用capId下载验证码图片
1
2https://captcha.95516.com/media?mediaId=me1fed7b26f764a94b37767aeb2bf22a7.png
https://captcha.95516.com/media?mediaId=se1fed7b26f764a94b37767aeb2bf22a7.png提交验证结果,获取
token,sign1
2
3
4
5
6
7
8
9
10
11
12
13
14
15https://captcha.95516.com/session/vfy?callback=jsonpCallback20220523170812896_OvDXVwf96RZaNwS&v=1653296892896&sesId=ac078fdd86e4459da107ad1bb4f3bdaa&passTime=88&value=169.05537459283386&bhv=E(!!H(!!()
HTTP/1.1 200 OK
Date: Mon, 23 May 2022 09:08:34 GMT
Content-Type: application/json;charset=UTF-8
Connection: close
Server: nginx
X-Frame-Options: SAMEORIGIN
X-Via: 1.1 dedxin32:7 (Cdn Cache Server V2.0)
X-Ws-Request-Id: 628b4f12_dedxin33_5004-51280
Content-Length: 210
jsonpCallback20220523170834203_JYAuk4D3QGsASX6({"resCode":"0000","resMsg":"成功","resData":{"sign":"c6f01502ec59311a373c6d076e05c156","token":"361ee9dc0fb143198b6a9006c8805c8e"},"extensions":{},"dealTime":5})提交抢券请求。
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64POST /youhui-web/restlet/frog/download HTTP/1.1
requestId: ff70a604db084df7a0b04b37dc370650
X-Tingyun-Id: 4Nl_NnGbjwY;c=2;r=1198351094;u=f6deeb5ff2e3dcaf1ec602c68c59b166a809eedc49e41d523e747935ab486eba4bf1714ff5a5c5606bf66ff5d7b5a07b::A8B29C5F57C4A663
X-Tingyun: c=A|CAtzD3av_OQ;
cityCd: 510100
nextdataDeviceId: 202111292255244eee4bfd2433484fe8c57cef421c9ea20194f1689290cc87
gpsLongitude: 104.071315
Accept: */*
User-Agent: Android CHSP
dcTagList: PY:AB,BS:AB,CT:AB,LF:AB,TV:AB,OP:AB,AD:AB,HP:AB,BL:AB,AC:AB,FD:AB,ID:AB,MB:AB
language: zh_CN
locale: zh-CN
key_session_id:
nonce: 491f056b-0201-4139-9c91-d7bafbc091d5
urid: 153044286065308
sid: 4f3a3b7983634f7d9a3a4243906b27b7a
timeStamp: 1653296914705
dfpSessionId: 110005D001k0kOPiNTF0pzlzb9KWP1653296888029
gray: 0
dcTag:
requestId: db81bc8c-6e5c-4146-ba5e-0f52e90a983e
digest: FA1287DC731274F5325E4C4E4121AB88465EBF5296C0E4EA1550E0DAB984AABC
gpsLatitude: 30.538696
Content-Type: application/json; charset=utf-8
Host: youhui.95516.com
Connection: close
Accept-Encoding: gzip, deflate
Content-Length: 448
A54CB6F38CCE2BDE2BA466F5E1DC14B6485648ED408B09C807848E80C1F74A9FC05AD76AF7E940BC03294275F0E3115B54AC1289C14215B96B295AC24129D4FFE8EE4FC6DCF6EA46B6058F33C6FD883AB111F19B13AD44B377082AAAC506C37CB8A2677ECBB2EE7747386CC70E39CB4AB5202347C97338E79574C02B53BDCFDF23B9D845E85E14A184DF2DA89B327F3A0A4B46C399F2E4A64650ADF026D38EA570B759A47075F74C6791488C6238887F545FF82E4D9A31FAE469F1DFB66266FC4D2CEBDA435294B525E0D09F3E3E885587585D98CC658B94C167B9B8872CE9CF
-----------------------------
HTTP/1.1 200 OK
Date: Mon, 23 May 2022 09:08:35 GMT
Content-Type: application/json
Connection: close
Server: nginx
X-Frame-Options: SAMEORIGIN
Access-Control-Allow-Origin: ââ
Access-Control-Allow-Methods: ââ
Access-Control-Allow-Headers: X-PINGOTHER, accept, content-type, isOutput, h5-user-agent, sid, urid, dfpSessionId, cityCd, gray,dcTag,nextdataDeviceId,gpsLongitude,gpsLatitude
Access-Control-Expose-Headers: date
Access-Control-Max-Age: 1728000
Access-Control-Allow-Credentials: true
X-Via: 1.1 PS-KWE-01Ber55:5 (Cdn Cache Server V2.0)
X-Ws-Request-Id: 628b4f12_PS-KWE-015vJ56_23355-42496
Content-Length: 208
1de6a613988fe573f7b73c0c41754e179c80706f59f307e55cd29e1b42507f72a53589c37ec3b0fa5d6939ae658dbb43062f28b5e1c9bf82a01807f61a1726354e9b8146ac17599831dd09c6d7f731217059a3729350ab5107ef975ebdd1909538f900d8739bba6e
解密:
encrypt:
arg0: {"verifyValue":"","billId":"3102022051863931","captchaTp":"2","verifyCode":"","token":"361ee9dc0fb143198b6a9006c8805c8e","cityCd":"510100","sesId":"ac078fdd86e4459da107ad1bb4f3bdaa","sign":"c6f01502ec59311a373c6d076e05c156"}
encrypt result:
A54CB6F38CCE2BDE2BA466F5E1DC14B6485648ED408B09C807848E80C1F74A9FC05AD76AF7E940BC03294275F0E3115B54AC1289C14215B96B295AC24129D4FFE8EE4FC6DCF6EA46B6058F33C6FD883AB111F19B13AD44B377082AAAC506C37CB8A2677ECBB2EE7747386CC70E39CB4AB5202347C97338E79574C02B53BDCFDF23B9D845E85E14A184DF2DA89B327F3A0A4B46C399F2E4A64650ADF026D38EA570B759A47075F74C6791488C6238887F545FF82E4D9A31FAE469F1DFB66266FC4D2CEBDA435294B525E0D09F3E3E885587585D98CC658B94C167B9B8872CE9CF
decrypt:
arg0: 1de6a613988fe573f7b73c0c41754e179c80706f59f307e55cd29e1b42507f72a53589c37ec3b0fa5d6939ae658dbb43062f28b5e1c9bf82a01807f61a1726354e9b8146ac17599831dd09c6d7f731217059a3729350ab5107ef975ebdd1909538f900d8739bba6e
decrypt result: {"msg":"验证码非秒杀时间内生成,请重试","resp":"E11","cmd":"frog/download","params":{}}
1 | |
1 | |
1 | |
1 | |
1 | |
1 | |
1 | |
1 | |
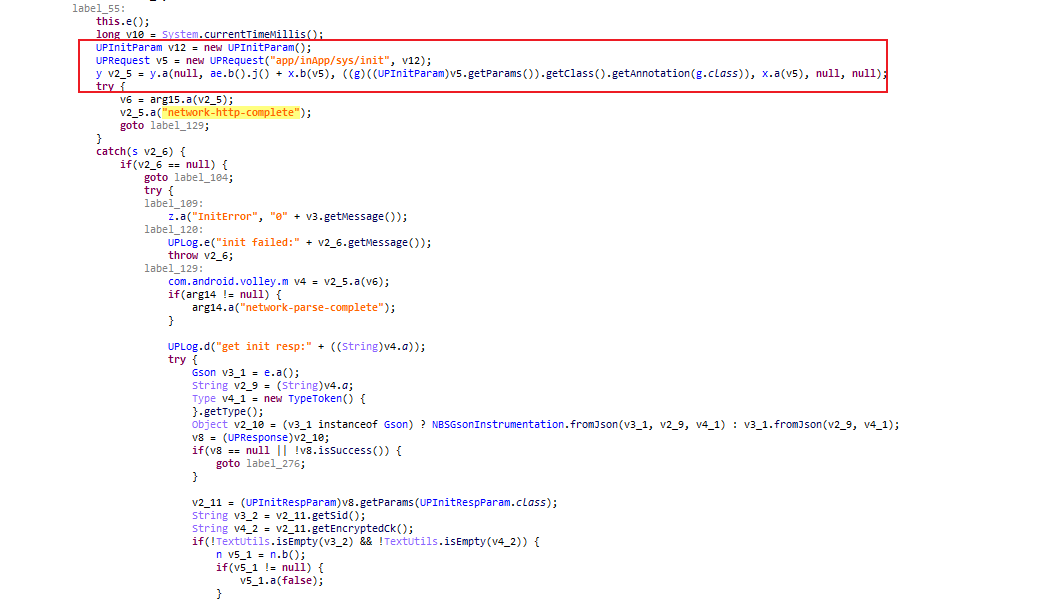
digest
1 | |
HOOK方式获取密钥
1 | |
Frida内存搜索、调用
1 | |
Python抢券
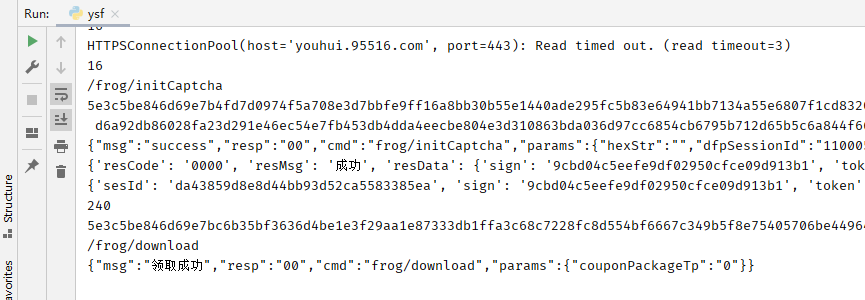
滑动验证码“漏洞”
请求滑动验证码数据时,返回了需要滑动的距离(capAnswer)。
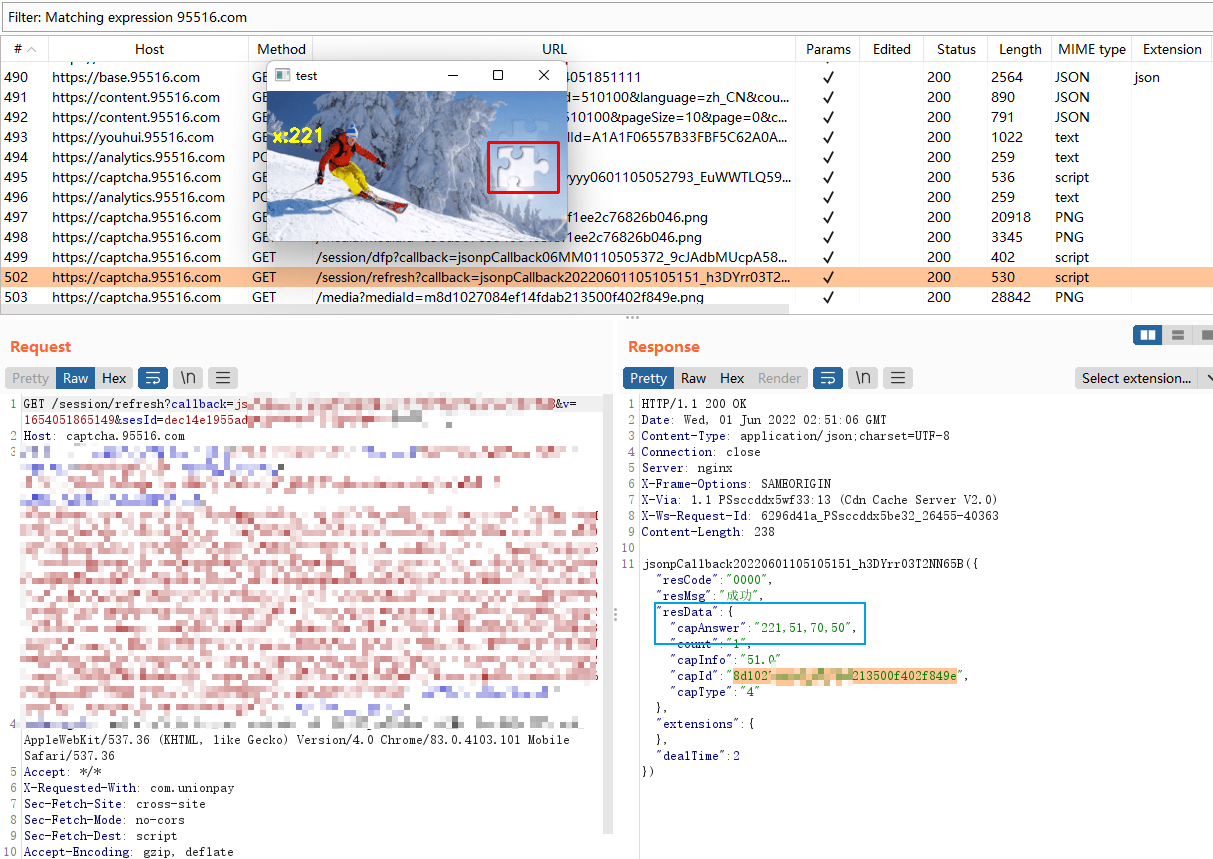
2023.04.10 更新
老版本(v9.0.6)被强制升级,更新了目前google play上的最新版本,和iOS一样使用了SM4-CTR代替了3DES加密。
1 | |
1 | |
1 | |
内存搜索sm4_key:
1 | |
请求签名
签名这部分没有变化,依旧是SM3。
1 | |
1 | |
2023.06.21 更新获取encryptedVid与请求头
获取encryptedVid
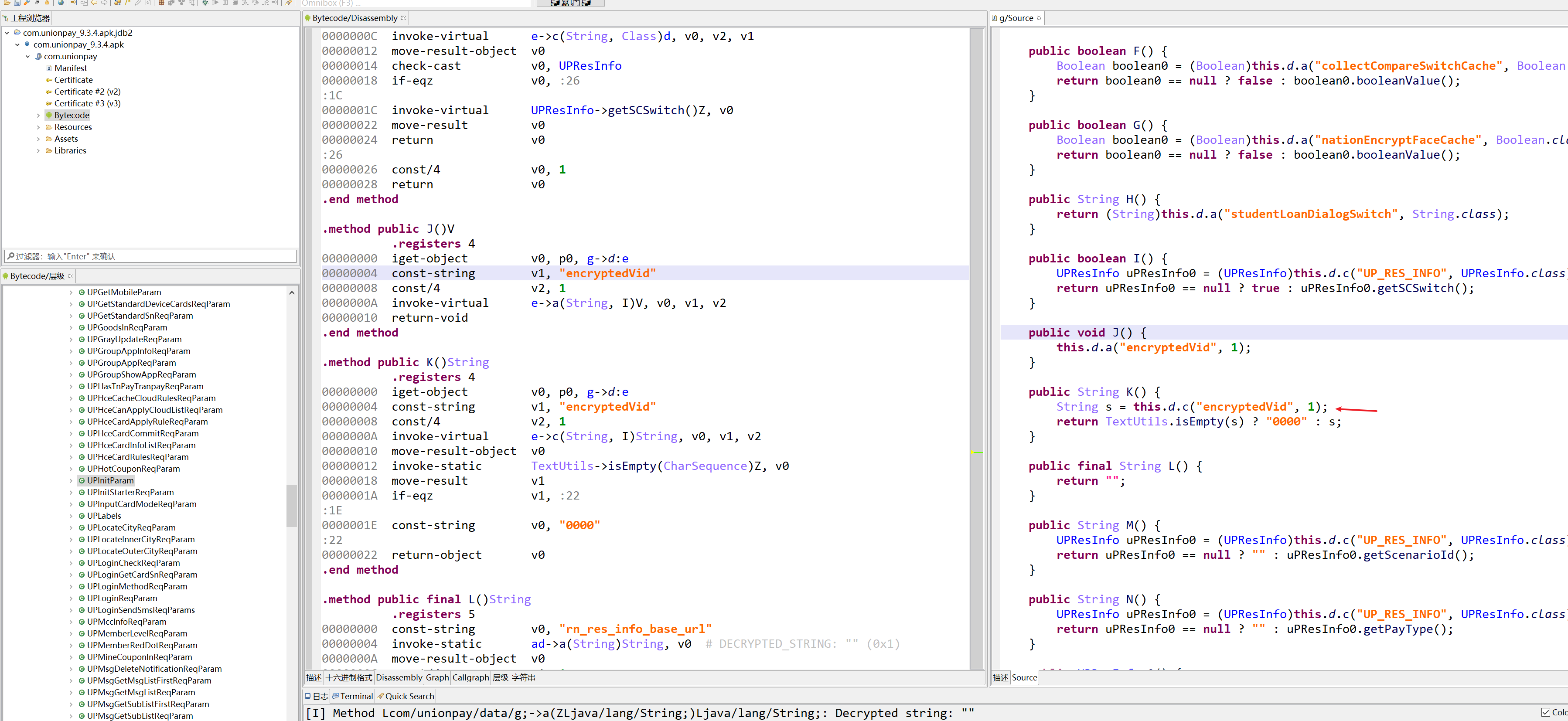
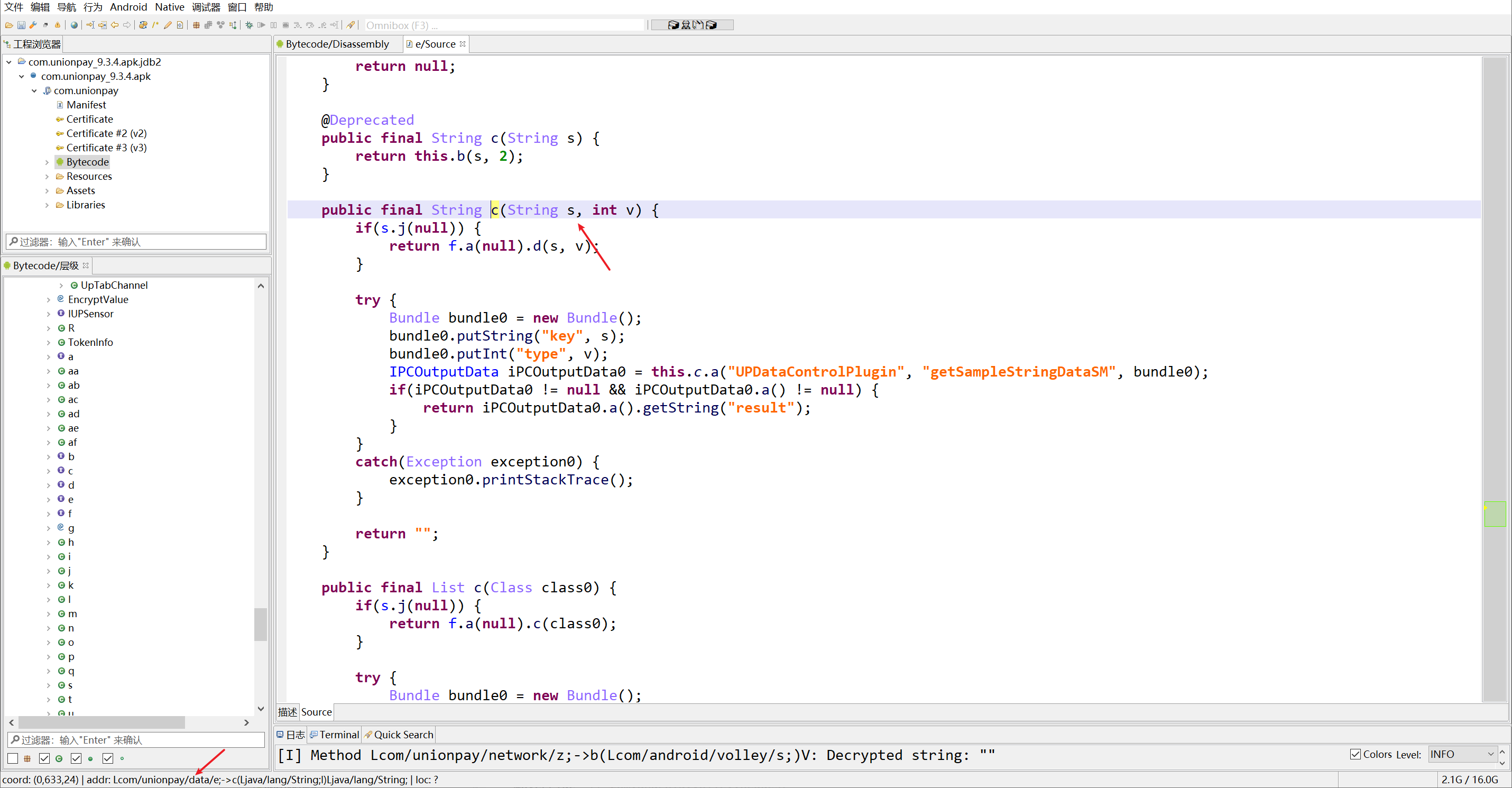
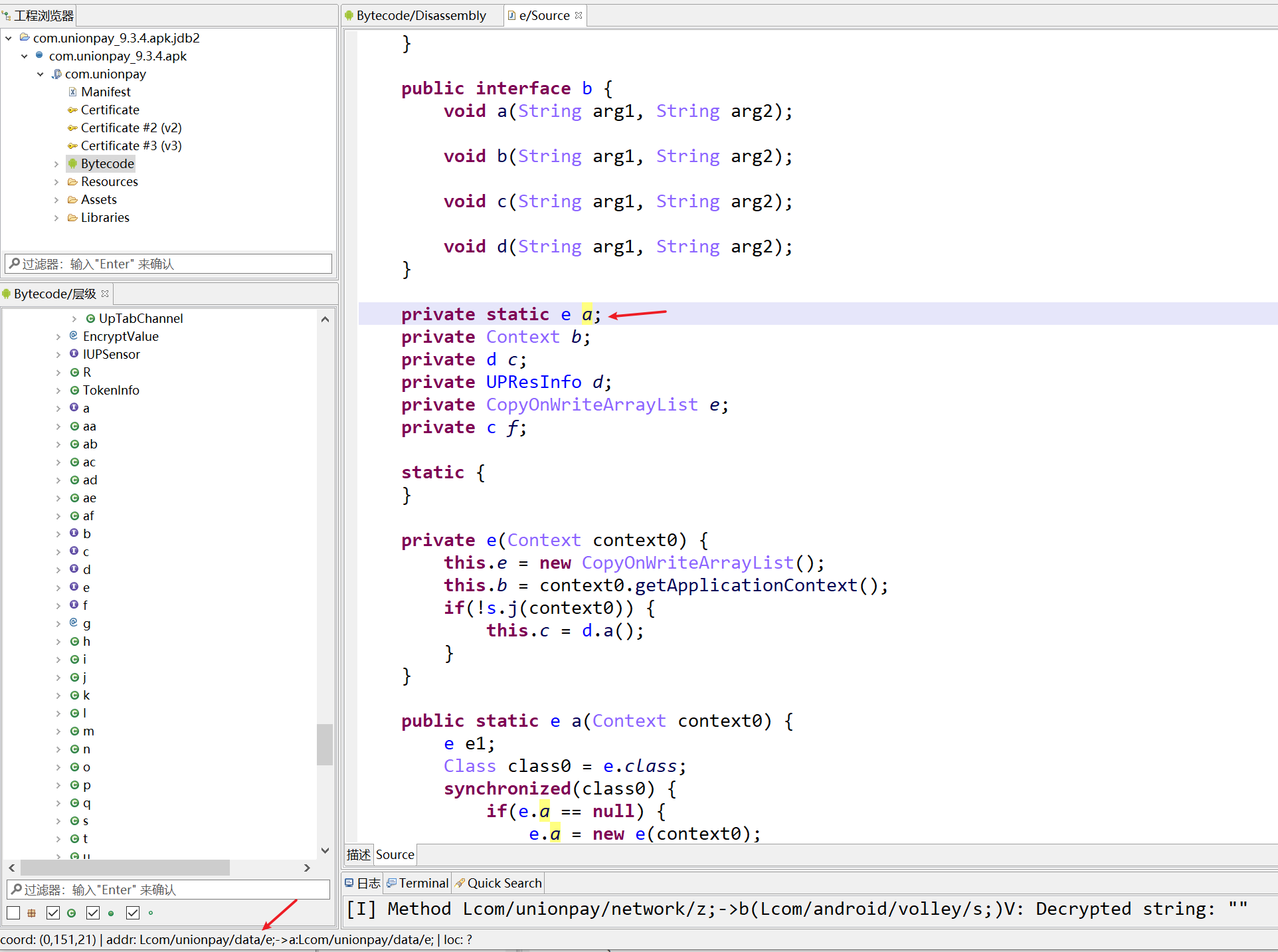
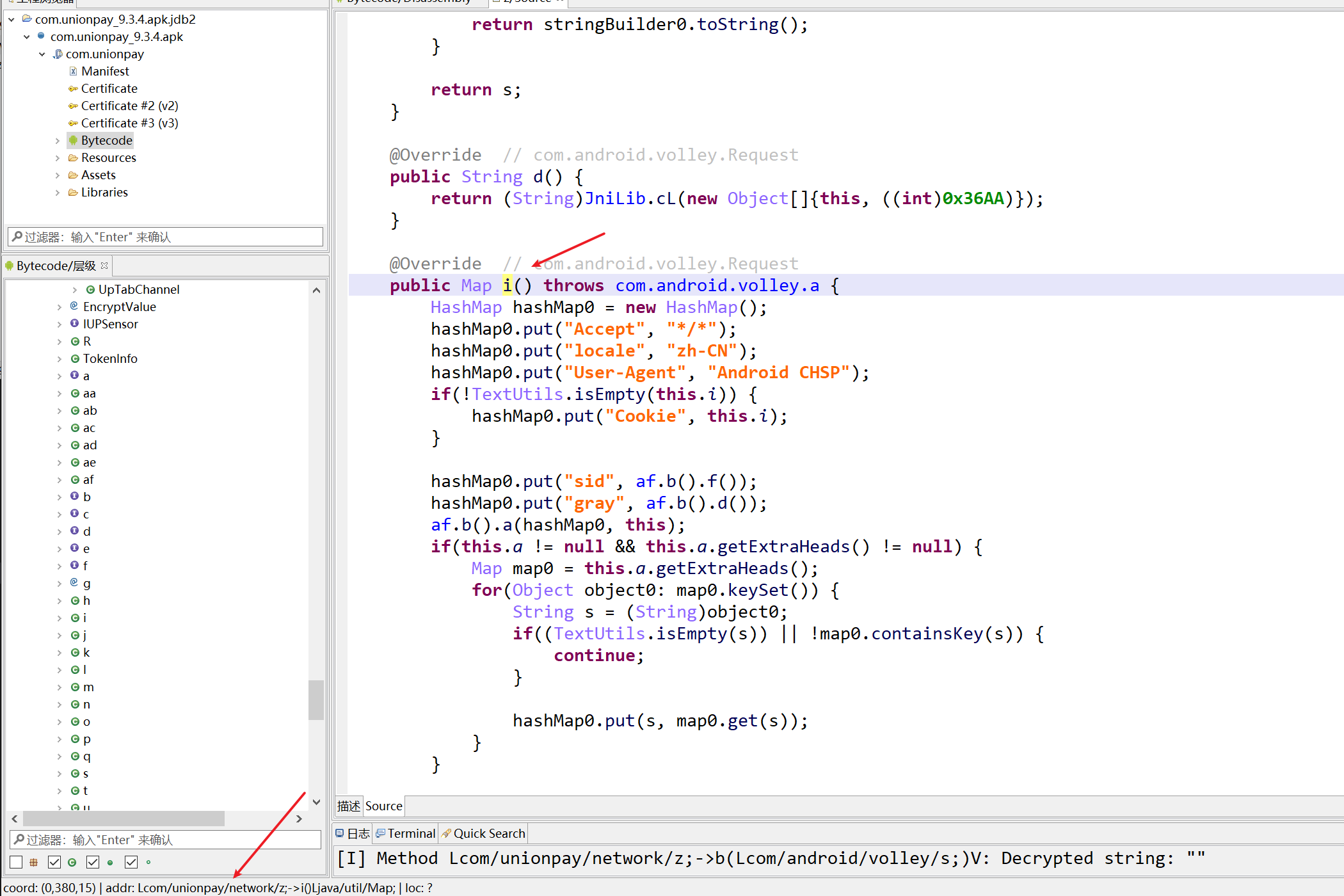
获取请求头
1 | |