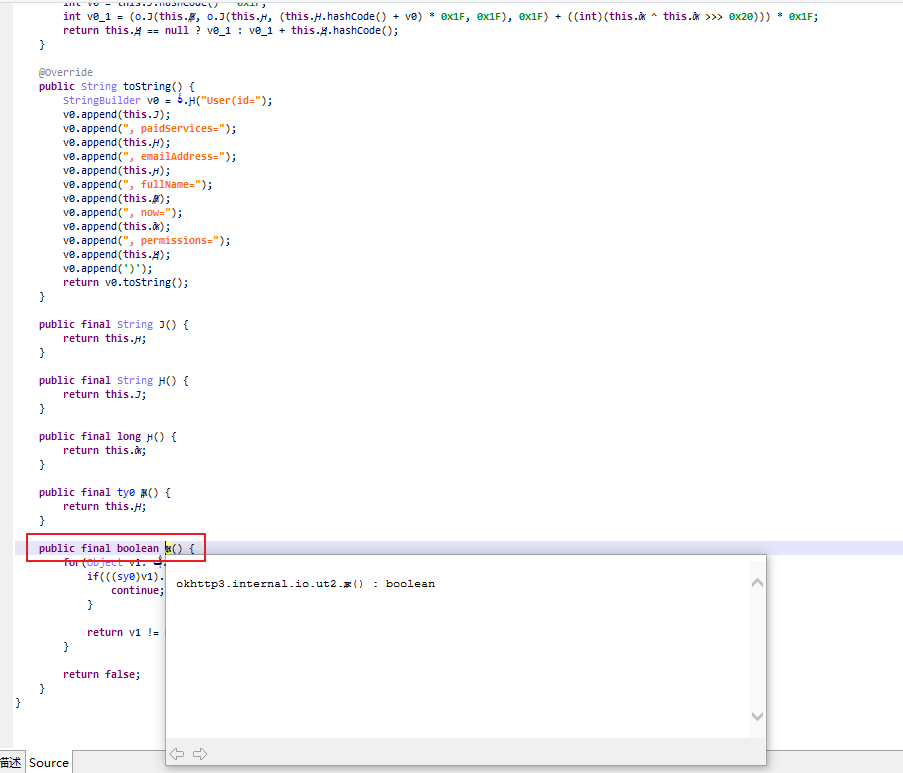
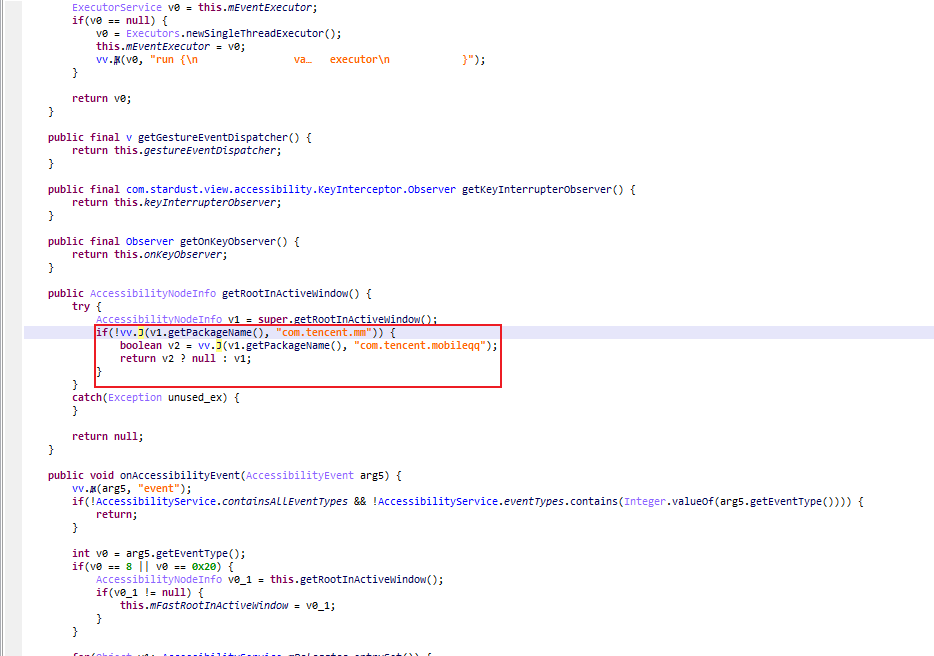
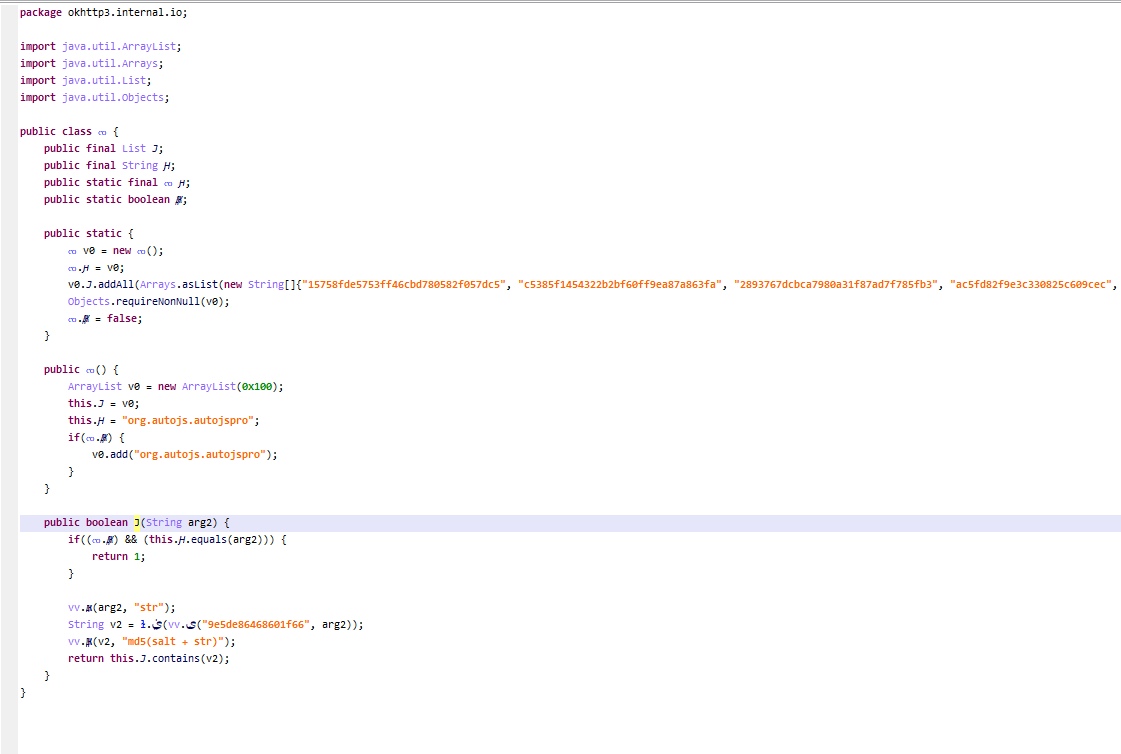
.text:001EB350 2D E9 F0 4F PUSH.W {R4-R11,LR}
.text:001EB354 85 B0 SUB SP, SP, #0x14
.text:001EB356 06 46 MOV R6, R0
.text:001EB358 50 20 MOVS R0, #0x50 ; 'P'
.text:001EB35A 10 70 STRB R0, [R2]
.text:001EB35C D6 F8 98 40 LDR.W R4, [R6,#0x98]
.text:001EB360 0C B3 CBZ R4, loc_1EB3A6
.text:001EB362 20 68 LDR R0, [R4]
.text:001EB364 F8 B1 CBZ R0, loc_1EB3A6
.text:001EB366 60 68 LDR R0, [R4,#4]
.text:001EB368 93 46 MOV R11, R2
.text:001EB36A 03 91 STR R1, [SP,#0x38+var_2C]
.text:001EB36C D0 F8 00 80 LDR.W R8, [R0]
.text:001EB370 D1 E9 00 50 LDRD.W R5, R0, [R1]
.text:001EB374 00 69 LDR R0, [R0,#0x10]
.text:001EB376 6A 6B LDR R2, [R5,#0x34]
.text:001EB378 D0 F8 2C A0 LDR.W R10, [R0,#0x2C]
.text:001EB37C 95 F8 58 00 LDRB.W R0, [R5,#0x58]
.text:001EB380 D2 F8 4C 90 LDR.W R9, [R2,#0x4C]
.text:001EB384 C0 07 LSLS R0, R0, #0x1F
.text:001EB386 01 92 STR R2, [SP,#0x38+var_34]
.text:001EB388 0F D1 BNE loc_1EB3AA
.text:001EB38A A9 69 LDR R1, [R5,#0x18]
.text:001EB38C D1 F8 D8 00 LDR.W R0, [R1,#0xD8]
.text:001EB390 58 B1 CBZ R0, loc_1EB3AA
.text:001EB392 D1 F8 B0 10 LDR.W R1, [R1,#0xB0]
.text:001EB396 02 29 CMP R1, #2
.text:001EB398 07 D1 BNE loc_1EB3AA
.text:001EB39A D0 F8 20 05 LDR.W R0, [R0,#0x520]
.text:001EB39E 01 69 LDR R1, [R0,#0x10]
.text:001EB3A0 40 69 LDR R0, [R0,#0x14]
.text:001EB3A2 00 91 STR R1, [SP,#0x38+var_38]
.text:001EB3A4 04 E0 B loc_1EB3B0
.text:001EB3A6
.text:001EB3A6
.text:001EB3A6 loc_1EB3A6
.text:001EB3A6
.text:001EB3A6 00 24 MOVS R4, #0
.text:001EB3A8 5A E0 B loc_1EB460
.text:001EB460 loc_1EB460
.text:001EB460 20 46 MOV R0, R4
.text:001EB462 05 B0 ADD SP, SP, #0x14
.text:001EB464 BD E8 F0 8F POP.W {R4-R11,PC}