from flask import Flask
from flask import request
from flask import Response
import M2Crypto
import base64
from M2Crypto import *
from base64 import b64encode, b64decode
import time
app = Flask(__name__)
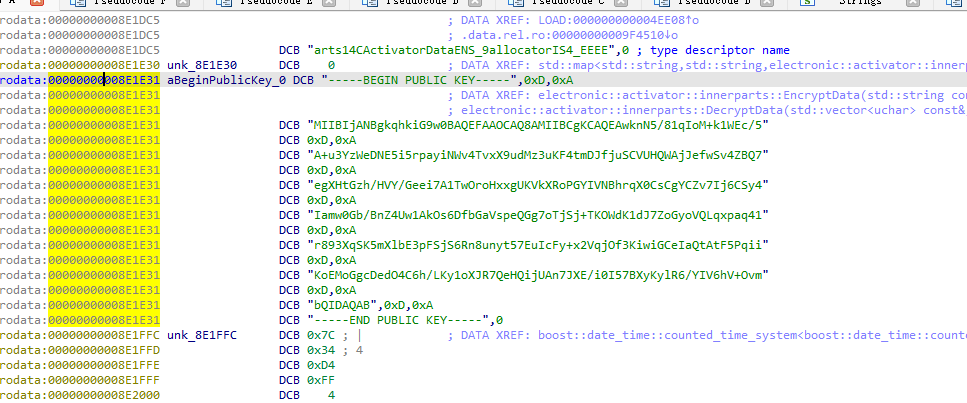
PRIVATE_KEY = '''-----BEGIN PRIVATE KEY-----
MIIEvgIBADANBgkqhkiG9w0BAQEFAASCBKgwggSkAgEAAoIBAQDWPlOH/MubSS5m
JCHUsKDZQdZ3cAVnJBLVru3CR67FHD0XN5HaaTz8Hc73A/38H87XV3eGkk7Fk1LA
YC4OksfoI6KbD0QsRikZpECi8WjJoEdxyGgG29W2oi04AJsUWfw3zqYWxvnzitGT
CGO814fw+m62/0DwoHByJkoiZ9KiCv03ee9cqXKreIyyvdRqreM7NUjyQe7RANqv
uSekPGrN1NtY8aONv5cc/ZR30gvRsgoPEOTrMUqi+0BXcDZoSXJU4pbe1rYeYtjr
IWiYnR96fVKe4SXph5a19K6oMzT1B/X8Y30zIJ15sBeJKMaqdHg9/KTSlyf26eis
gnyuICS7AgMBAAECggEABTAfL7TUbV85S2nmk9LvIjOw8NV6nAPInPoOcdzwg39q
j0xeMM7JlkVWhK7JELjodlh84Xpbg/dMUrJBi0LMqndqcZzOBtBwIFnU4t07r149
PKkgs8HRDAojVC7XkoeXTvanGPgah2Y+KvRSDfmeJhy6X54QwYLxFiKNOwYOmLPm
EhWLXwxgtyD7aVCstaxM9vFWoBNBEz5S876SeEkMb8tvJbeM0DGJMyQU0jdPE2jm
RJUomQeI/e/Mw1Pn7YtfMarO5hWQ/xQwvIyIGYN4UEiFZuAGxxWHwwZ6IYGAWD6z
w1ldVNC7OmKDA3GCVSsXmDCycKyLwpbavZ+m6qaBMQKBgQDzWde4TRcEQoWBZ6V4
W6yd6mpaeQr0JWrOcAYCGDIfjDw12eqUyGPrVonnQlGQ9IOTrG2NWH+VYTqXyTpY
/kpZDP3mfdJFENSShjZcaSVTCV70Ff/iq+W7dlrYYxn3vb6gL3W3vyw9UDaPh2hw
oG8K+/a6tW2oCSBoUz49fMLUiQKBgQDhYSn3FhCdRQajCelqCVuAejNehIakczls
ik1TOI8Y892JFMXNe0KaungzDIILxC6s/elSYXkVpP4BQXrdV2W8CXc6o7mUmTh8
zEZn9sGLooGgSRfXd6eG9GRBtJ+ij1rBYu1Ww8sSttMn33ga4+IjVQK/d9IpHzXZ
UKddobrmIwKBgQCLr6+fMEkc/d5KqKcYDm9oei2wXzjFalEDzNP2EdN7vnC1bLA1
1U1dwmAIak4Nyf1ZICoGb51UruoGRNEEUnt04HtB+klfsciDjxzXMNfm8UMbEyG+
CHQnhkmhWkmGptksc/G7lrYbP9cBznVJ6R20jWtUQ159jTeYCuh4PQxNGQKBgHGD
bo90HYoYae9T3qv5aoya/6RrOyU4o4N3ZNq1cd0vdjTEsZt8qV8k68VKV3V1qcyX
VhyX21R7dTNMt4Ujr6m1Wse+Doo5Yan5eLyEG5cokgEYz1lGeqoODTDKuFw3t44P
NVqt4mnaix9Z/jQM8qi4+FlXEBKGFakOZj1SZ7/hAoGBAKgINEQpqzqT37VGWaFA
39OsHOusmBaC7m+vzjuTalsW6OvzgYNQZNu7InJqfWKMEtgVu8vnXpcgtKW19ofj
AREgbn9sTya217y4MIn/o7DE5p21PAi142rKx4N2m1IC/cmlTvafTWnlWFNvmIeX
6pZ3LUcHEk8u9dV6Vm+DfljM
-----END PRIVATE KEY-----
'''
def rsa_pkcs1_encrypt(plaintext, private_key):
"""
RSA私钥加密
:param plaintext: 明文
:param private_key: 私钥
:return:
"""
max_encrypt_block = 245
padding = RSA.pkcs1_padding
plainBytes = plaintext.encode(encoding='utf-8')
plaintext_length = len(plainBytes)
if plaintext_length < max_encrypt_block:
return b64encode(private_key.private_encrypt(plainBytes, padding)).decode(encoding='utf-8')
offset = 0
ciphers = []
while plaintext_length - offset > 0:
if plaintext_length - offset > max_encrypt_block:
ciphers.append(private_key.private_encrypt(plainBytes[offset:offset + max_encrypt_block], padding))
else:
ciphers.append(private_key.private_encrypt(plainBytes[offset:], padding))
offset += max_encrypt_block
return b64encode(b"".join(ciphers)).decode(encoding='utf-8')
def reg(hid, license_key_code):
l = ['hid={}'.format(hid),
'&license_key_code={}'.format(license_key_code),
'&licenseName=Single License, 1 shared USB device ',
'&product_id=123',
'&product_name= USB Network Gate',
'&product_version=10',
'&serverDate=2022-09-12',
'&activationDate=2022-09-12',
'&nextActivation=2099-09-15',
'&firstActivation=2022-09-12',
'&errorCode=0',
'&key_type=2',
'®isted_name=test test2',
'&license_options=1',
'&key_options=14000',
'&serverTime={}'.format(int(time.time())),
'&activation_param=',
'&subscription=0',
'&hash=99b06159bc364aa8dc7d8b0a105be8e5']
bio = M2Crypto.BIO.MemoryBuffer(PRIVATE_KEY.encode())
rsa_pri = M2Crypto.RSA.load_key_bio(bio)
encrypt_data = b''
for msg in l:
primsg = rsa_pkcs1_encrypt(msg, rsa_pri)
encrypt_data += base64.b64decode(primsg.encode())
return base64.b64encode(encrypt_data).decode()
@app.route('/')
def index():
return __file__
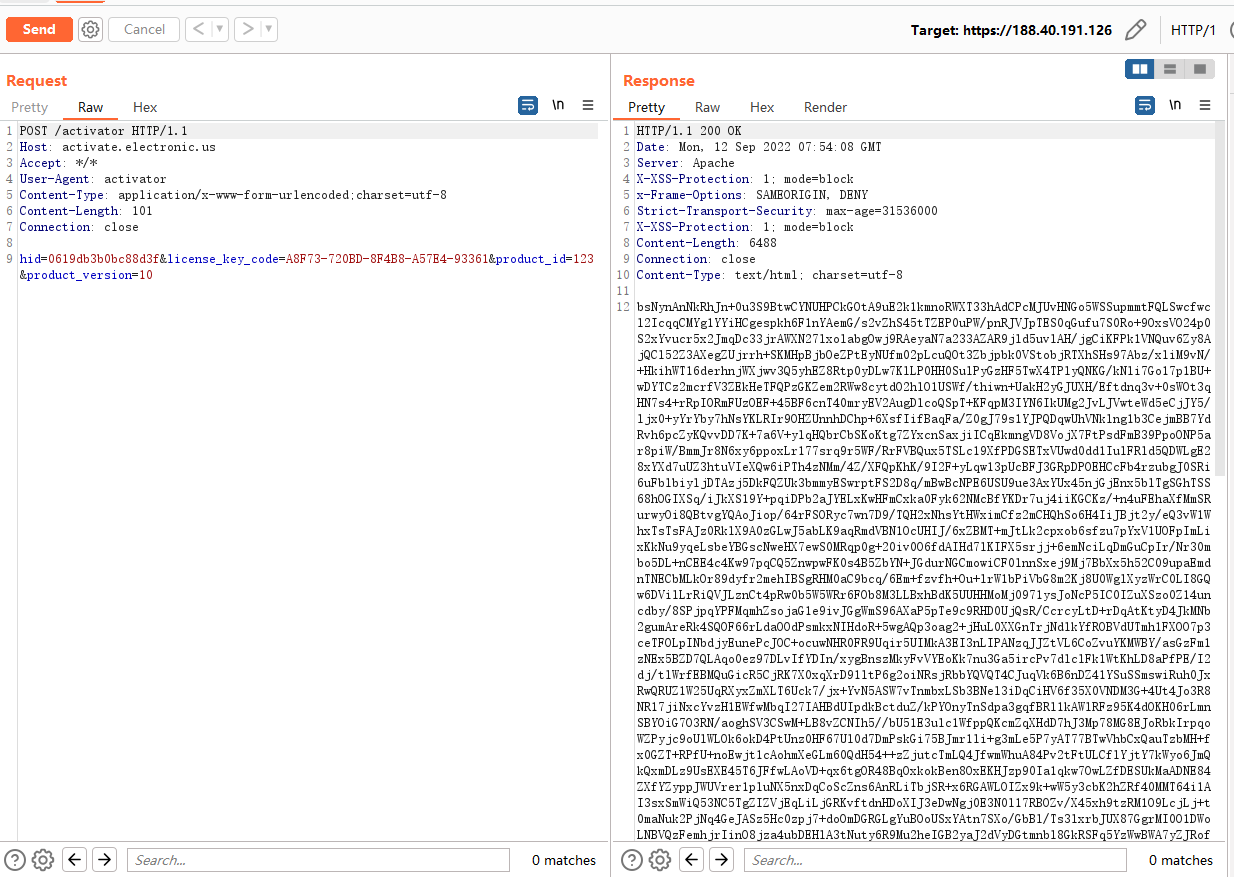
@app.route('/activator', methods=["POST"])
def activator():
hid = request.form.get('hid')
license_key_code = request.form.get('license_key_code')
if hid is None or license_key_code is None:
return 'error'
data = reg(hid, license_key_code)
return data
if __name__ == '__main__':
app.debug = False
app.run(host='127.0.0.1', port=9002)