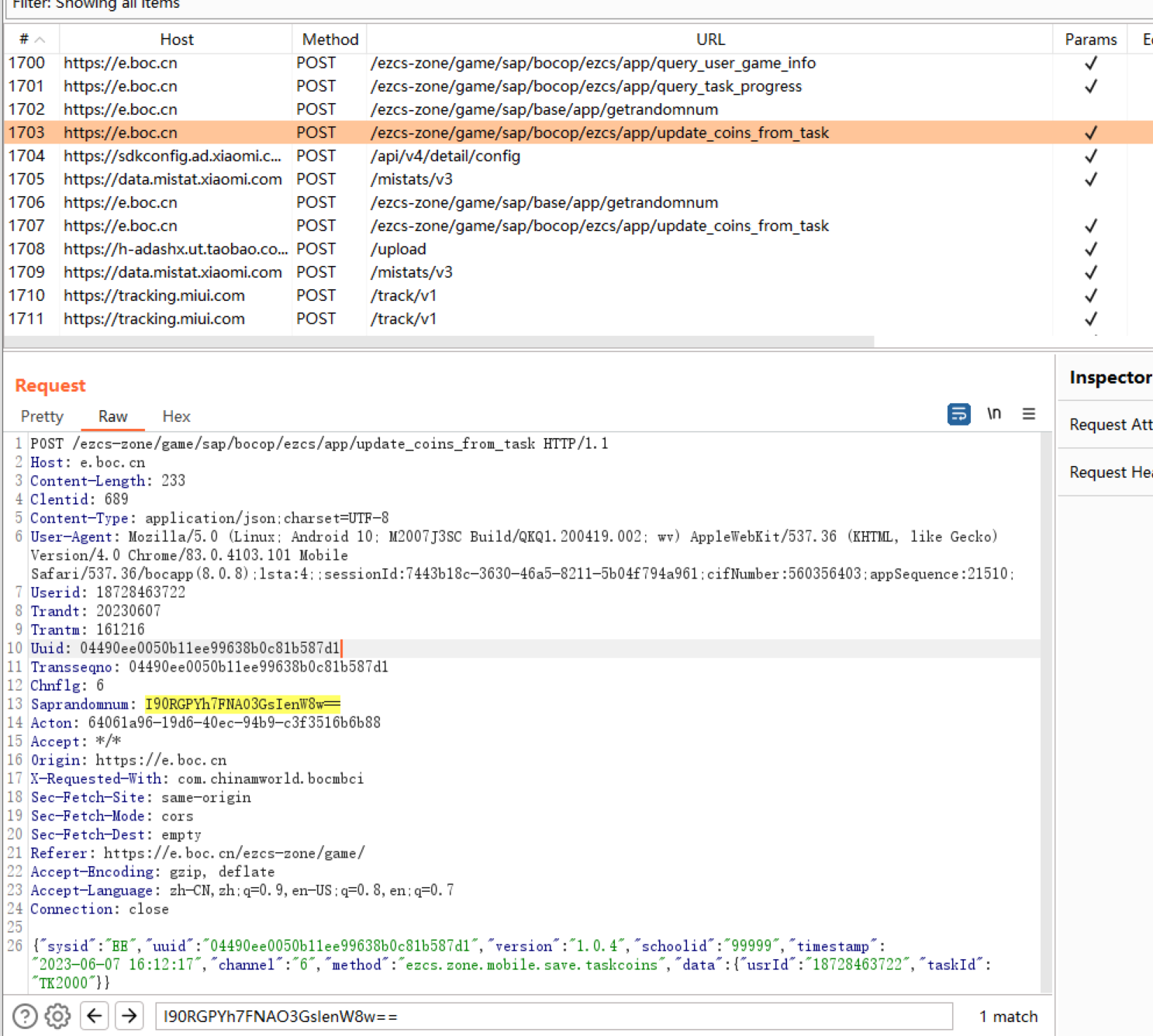
中国银行App saprandomnum参数逆向 分析 绕过frida,xposed检测后可以用插件开启webview调试。
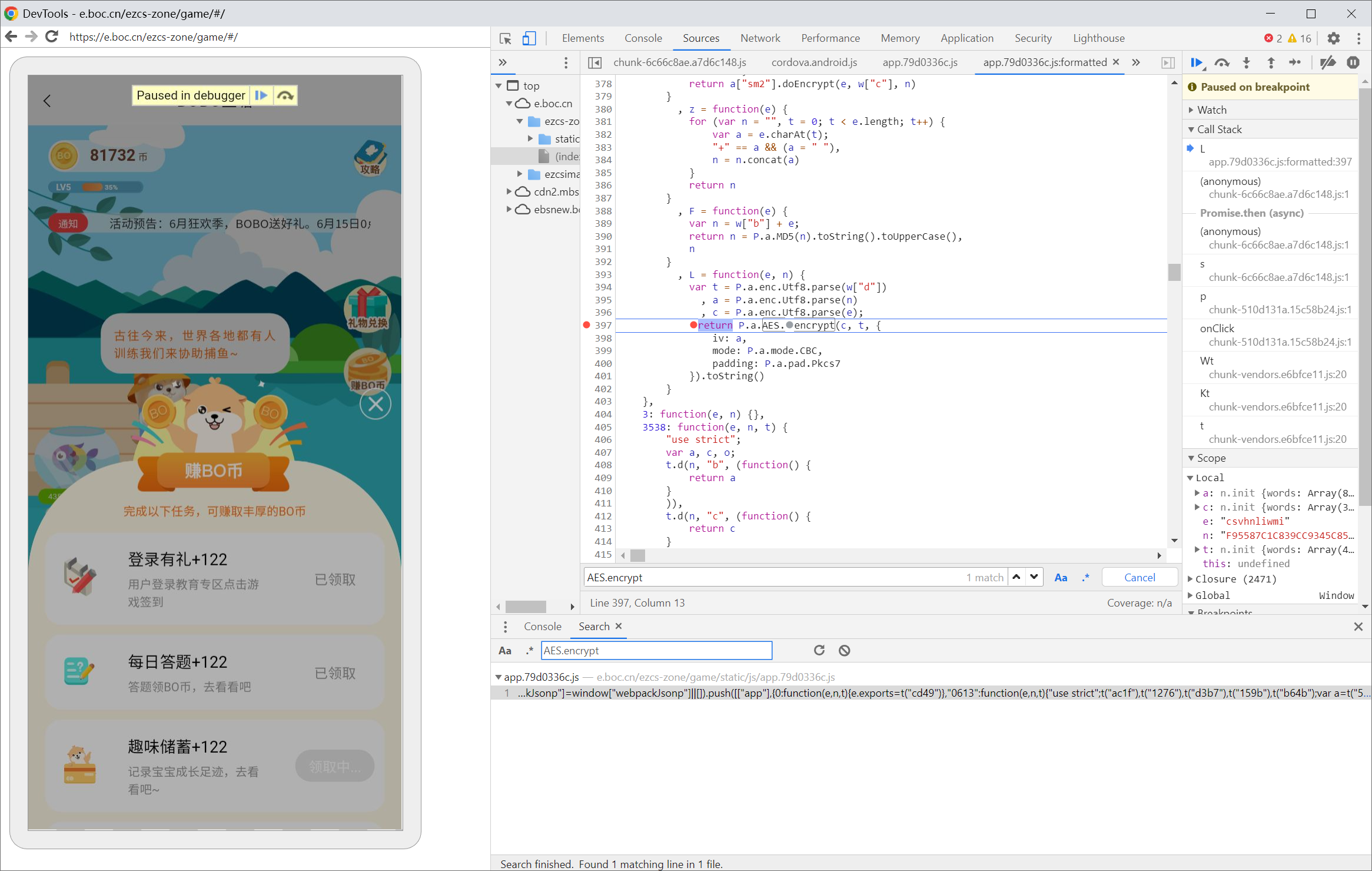
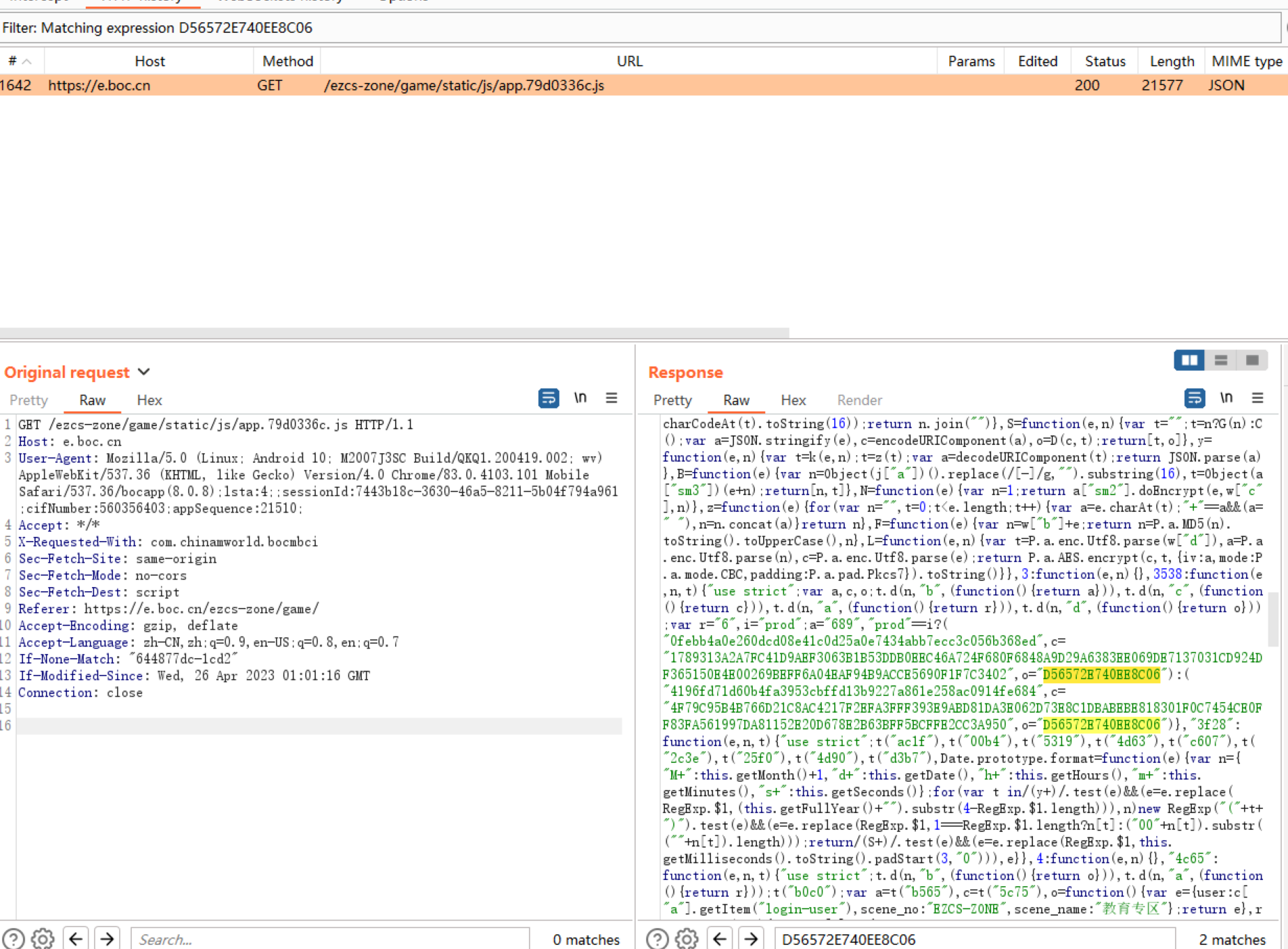
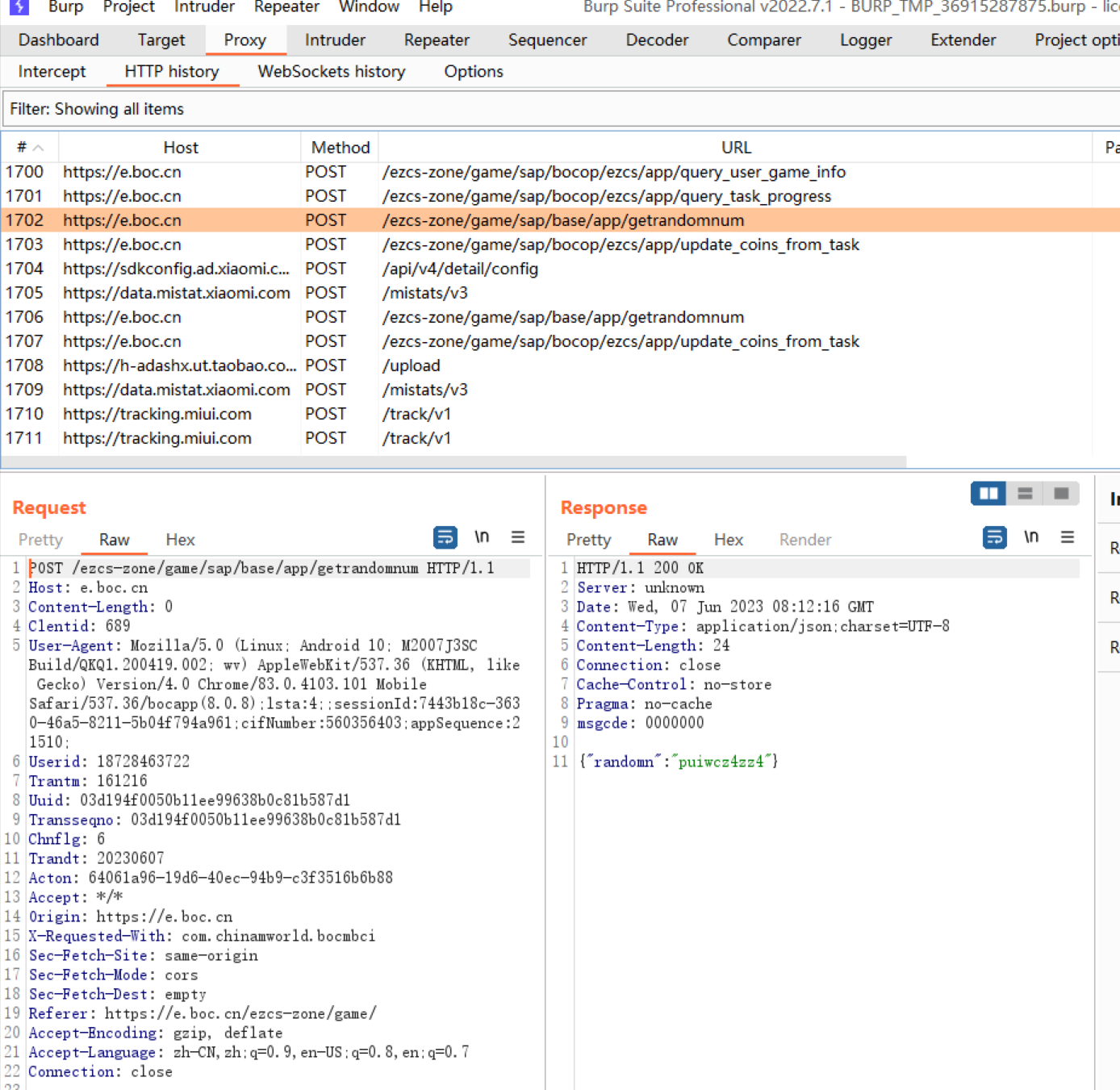
saprandomnum是由AES加密/ezcs-zone/game/sap/base/app/getrandomnum响应后的结果。
AES加密的KEY(repeatPublicKey)固定,IV是”clientId”+userid MD5后的结果。
{"clientId" :"689" ,"clientSecret" :"0febb4a0e260dcd08e41c0d25a0e7434abb7ecc3c056b368ed" ,"channelFlag" :"6" ,"publicKey" :"1789313A2A7FC41D9AEF3063B1B53DDB0EEC46A724F680F6848A9D29A6383EE069DE7137031CD924DF365150E4E00269BEFF6A04EAF94B9ACCE5690F1F7C3402" ,"repeatPublicKey" :"D56572E740EE8C06" }
A = function (e, t ) var a = l.a.enc.Utf8.parse(s["repeatPublicKey" ])return l.a.AES.encrypt(i, a, {
function (e ) var t = s["clientId" ] + e; return t = l.a.MD5(t).toString().toUpperCase(),
md5 ("689" +"18728463722" ) "F95587C1C839CC9345C85B0348DFEDA8"
代码及验证 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 from Crypto.Cipher import AESfrom Crypto.Util.Padding import pad, unpadimport base64import hashlibdef md5 (s ):if not isinstance (s, bytes ):return hashlib.md5(s).hexdigest().upper()def get_saprandomnum (userid, randomn ):'689' 0 :16 ].encode()b'D56572E740EE8C06' 16 ))return saprandomnum'18728463722' 'puiwcz4zz4' print (saprandomnum)